No Access to vCenter VAMI
If the the UI (the vcenter FQDN hostname:5480) loads but you cannot login knowing the password is 100% accurate because for example you can login to the console or using SSH tool like Putty for remote access.
The UI loads but login attempts fails to VAMI. This could be caused by the application service not being started.
Using the console or putty for access, login and run the following command to start the service.
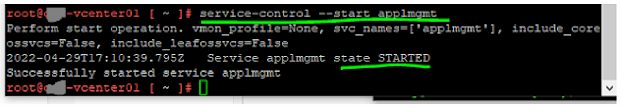
# service-control --start applmgmt
From the screen shot you could see that the command runs, starts the application management service and indicates the status as STARTED.
This process worked for me perfectly however, during the process the root user for vcenter had been locked out do to too many failed login attempts. of course because repeated attempts to access VAMI UI, thinking it was the incorrect password or the password had been changed for root access, incorrect passwords were entered.
The root account will lockout after 3 bad login attempts . The default timeout before the account unlocks is 5 minutes for the root account of vcenter. As long as the default has not been changed, wait another five minutes before trying to login even to the console for access or through Putty for access.
You may also try the following command to reset the root password lock or wait 5 minutes.
pam_tally2 -–user=root --reset
You can check if the default is still the lock out value.
cat the file .
/etc/pam.d/system-auth
Look for root_unlock_time=300 in the output . The value of 300 means five minutes so just be patient.
Sorry I don't have a screen shot for that step. My session had timed out and it was lost. I know, i could have just re-created the problem to get the screen shot but didn't want to lock my root account again for a screen shot and i had to move on. It safe to say that readers of this post will have the technical experience to manage without that screen capture.
Provide better support to your end users and clients. Whether you're a one person business servicing your clients from small office or home, or a mid-sized to large MSP provider of remote IT services, 4RemoteSupport software for online desktop support improves the level of service. Most MSP and and individual tech support services provide remote access support using more than one support software.
Remote access software that requires an agent installed on remote computers for re-connections often costs more than software for online desktop sharing when required only. Agent based keeps a service running and usually incurs a charge per remote desktop. Non-agent based remote desktop client software permits remote desktop connections when needed and usually and triggered by the remote desktop user. Most providers have both types of support tools used for different situations. 4RemoteSupport online desktop support software doesn't require any software or framework services preinstalled. It works with all browsers. No browser extensions or plugins needed.