 For those of you searching the Internet to try and find a good or simple example of how port forwarding is done on a Cisco ASA 5500 series firewall (in this example, it is a Cisco ASA 5505 version 7.2) This post contains a working example of a port forwarding configuration on a Cisco ASA 5505 that's allowing RDP, TCP port 3389, through the firewall to from the Internet to the LAN side to a server. For new users to the ASA, how to configure a port forwarding rule on a Cisco ASA 5505 can be a more easily accomplished if the working configuration of a working ASA5505 is viewed. For many of the more seasoned users of the Cisco security appliance, port forwarding is very easy and need not be searching for answers.
For those of you searching the Internet to try and find a good or simple example of how port forwarding is done on a Cisco ASA 5500 series firewall (in this example, it is a Cisco ASA 5505 version 7.2) This post contains a working example of a port forwarding configuration on a Cisco ASA 5505 that's allowing RDP, TCP port 3389, through the firewall to from the Internet to the LAN side to a server. For new users to the ASA, how to configure a port forwarding rule on a Cisco ASA 5505 can be a more easily accomplished if the working configuration of a working ASA5505 is viewed. For many of the more seasoned users of the Cisco security appliance, port forwarding is very easy and need not be searching for answers.Since the RDP protocol and the services running on windows XP and Vista client machines are derivatives of Microsoft's Terminal Server, the proceedure for setting up a port forward configuration for Microsoft terminal server is the same. The Cisco ASA5505 is not concerned what you are connecting to behind it, it's just concerned that its own configuration allows the right data and connection to go through.
Below is a GUI shot of a working RDP (Terminal Server) port forward configuration running on a Cisco ASA 5500 series firewall. The TCP port number 3398 is forwarded from the outside interface that's part of VLAN2 to the inside interface that's part of the VLAN1.
!
interface Vlan1 nameif
inside security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Vlan2 nameif
outside security-level 0
ip address dhcp setroute
Using the example below, just swap out the ip addresses shown in the static NAT translation for port forwarding RDP (terminal Server) with your own and you have a connection from the Internet to the LAN.
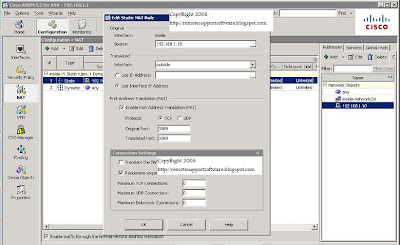

If you prefer command line, it's three lines of code at the command line that will do a simple port forwarding for RDP on the Cisco ASA.
Here they are:
access-list outside_access_in extended permit tcp any interface outside eq 3389
static (inside,outside) tcp interface 3389 192.168.1.10 3389 netmask 255.255.255.255
access-group outside_access_in in interface outside
Obviously, if you are looking to use the lines of code shown in the example above, change the 192.168.1.10 ip address shown above to be the address of the computer or server your forwarding RDP (terminal server) port to connect to. You can essentially use this example for terminal server RDP or for any other forwarding requirement you may have like ftp, http,smtp, etc.
Link to this post:
http://remotesupportsoftware.blogspot.com/2008/10/configure-rdp-port-forwarding-on-cisco.html
Link to this blog:
http://remotesupportsoftware.blogspot.com
12 comments:
Thanks.
This port forwarding configuration can be used and applied for forwarding many other programs as the settings will be the same in the static NAT confiuration but the TCP port number will change.
Port forwarding Cisco ASA 5505.
This was a great little post that got right to the point and your right, once you see a working configuration it's easier then to follow along to configure your own. It also helps in understanding the way Cisco wants network people to think. Vendor terms differ and a field that reads one thing in the configuration of one manufacturers equipment may mean something just slightly different enough in another vendors equipment to mess up the config.
Port forwarding Cisco ASA 5505.
um... cannot even see the pics
Try again. There must have a been a problem with the site at the some. I've checked and the images are always visible. I've checked with FireFox 2 , FireFox 3, IE 7 and IE 6. I don't know if you are using a browser other than FireFox or Internet explorer but with those two browsers the images show. Displaying of images is a function of blogger.com. Once the images are uploaded, the site templates take over. There's nothing more that can be done to make the images display.
I see the images of the GUI interface for programming and configuring the Cisco ASA. The second image is a larger version of the image before it. it does display more clearly (for me). From you can see what section in the configuration to be in and what what to apply where for setting up a port forwarding rule on the Cisco ASA. I just swapped out the ip addresses shown with my own.
Thanks so much! I've searched all over the Inet for the past 3 or 4 days, and although I've found instructions claiming to forward ports, this is the only one that has worked, b/c it's thorough. All the instructions that I've come across don't tell you that you need to have...
access-list outside_access_in extended permit tcp any interface outside eq 3389
as well as...
access-group outside_access_in in interface outside
Thanks, again!
Your ALL welcome. Link and book mark the page so others can find it faster.
how to specify multiple public IP addresses that will be allowed access to rdp session. Rest of the world should be blocked
Hi,
you should update it because ADSM 6.4 has a new interface
++
Vincent
Hi all. thanks for the explanation, but it does not work on my version.
In the firewall status window it shows as "Deny tcp src outside:xxx.xxx.xx.197/62969 dst inside:XXX.XXX.XXX.XXX/4001 by access-group "outside_access_in" [0x0, 0x0]
I have the Static NAT Rule configured as in example and an Access Rule created inside outside / permit for service tcp/4001.
Any ideas ?
Thanks you really saved me with this post, I have just configured my ASA 5520 with ASA 8.21 and it works perfect.
One final question, if I want to delete those three lines, in case I want to modify anything and start over, do I use the "no" prefix and write each line again?
Regards,
Really very useful information and also very helpful. Maxmunus Solutions is providing remote support for the individual as well as for organization with support packages. which is required for an emergency.
For More Details:-http://www.maxmunus.com/page/Remote-Support
Post a Comment